Meer dan het salaris, de arbeidsvoorwaarden en het carrièreperspectief, is bij de strijd om talenten de mogelijkheid om makkelijk en flexibel te werken van...
Zeventig procent van de consumenten voelt zich comfortabel bij het idee om ooit in een autonoom vliegtuig te stappen. Dit blijkt uit een wereldwijd...
39% van de 55-plussers kunnen dagelijkse technologische uitdagingen niet meer de baas zonder hulp van hun kinderen. Iets minder dan de helft (47%) van...
Cybersecurity-bedrijf Fox-IT en ZyLAB, leverancier van slimme eDiscovery oplossingen, gaan nauwer samenwerken om juridische professionals en data privacy officers te ondersteunen bij het doorzoeken van digitale bestanden....
Thales heeft een groeiende security-kloof aan het licht gebracht. In Europa maakt meer dan 84% van de organisaties gebruik van digitale transformatietechnologieën zoals cloud, big...
Trouwe IT’ers die het afgelopen jaar in dienst bleven bij hun werkgever werden hier niet voor beloond. Hun salaris steeg slechts 2,3 procent. Dit...
Vandaag publiceert de Dutch Data Center Association (DDA) de vernieuwde Datacenter Gids 2019, met een overzicht van deelnemende colocatiedatacenters in Nederland. Met de Gids...
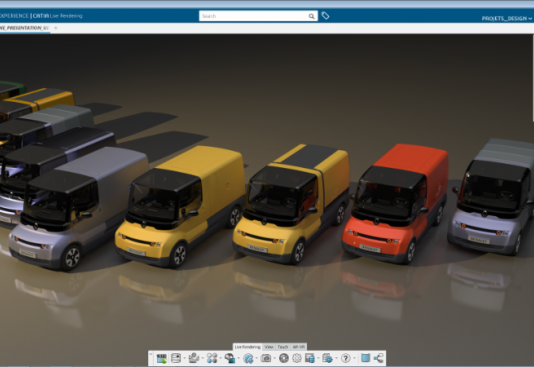
‘Het interne innovatielab van Renault heeft het 3DEXPERIENCE-platform van Dassault Systèmes toegepast bij het ontwikkelen van de experimentele EZ-FLEX elektrische auto voor vervoer over de ‘last mile’ in...
Woningen zijn als het aan de consument ligt in 2030 volledig duurzaam en ‘smart’. De consument verwacht onder meer thuisrobots en verregaande domoticavoorzieningen. Dat...
Zorginstellingen hebben er vertrouwen in dat zij adequaat kunnen reageren op een cyberaanval. Na de ransomware-aanval WannaCry die bedrijven wereldwijd platlegde (waaronder 15 ziekenhuizen...