What is virtual networking?
Virtual networking is the abstraction of network resources from the underlying physical network infrastructure. A virtual network is the logical representation of the physical hardware, such as the switches and routers, that makes up the infrastructure.
Virtual networks reside on an abstraction layer, each with its own workloads and security. While the virtual networks are isolated from each other, they can broadcast messages to each other via the virtual overlay network without the messages having to pass through the underlying physical devices.
Virtual networking uses the power of software to abstract network services from the underlying infrastructure and then connect network components in an overlay. Each network node is abstracted into a virtual entity. This abstraction enables network administrators to make configuration changes virtually without touching the physical devices.
How does virtual networking work?
With virtual networking, the physical networking — which comprises routers, switches and other devices — does not change. Instead, an overlay provides a virtual path or tunnel between devices and through networks. This overlay enables a programmatic approach to networking that eliminates a tremendous amount of infrastructure and redundancy.
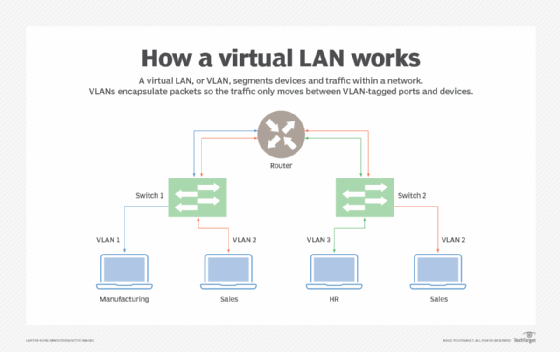
For instance, if an organization wanted to segment sales data and keep it from intermingling with manufacturing data, it would need two separate physical networks. But, with virtual networking, definitions for sales and manufacturing could be created on the same physical network, and data in motion can be kept separate.
Types of virtual networks
A network’s hardware devices usually define the three common types of virtual networks.
Virtual private network
A virtual private network (VPN) uses the internet as a transport, connecting two networks or connecting remote clients to central networks. VPNs create a secure, encrypted tunnel between two endpoints, ensuring privacy by obscuring traffic. Through a VPN, all network services on either side of the connection are presented as local services, but in between, they are hidden.
Virtual LAN
A virtual local area network (VLAN) enables the segmentation of devices or endpoints within a network, delivering better security and management through virtual segmenting of traffic. VLANs tag network traffic at Layer 2, encapsulating the packets so the traffic only moves between the VLAN-tagged ports and devices. Up to 4,000 VLAN segments can be supported on a network.
Virtual Extensible LAN
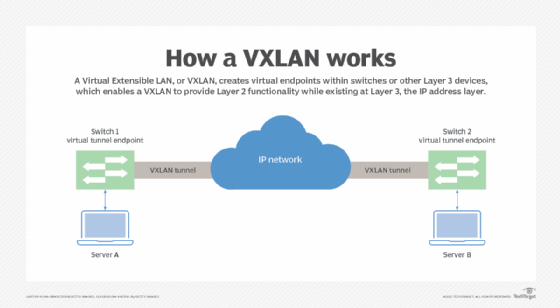
A Virtual Extensible LAN (VXLAN) can create the same type of virtual network as a VLAN, but it takes the VLAN concept further by encapsulating the media access control address in User Datagram Protocol.
Where a VLAN is defined over switchports, a VXLAN creates virtual endpoints within switches or other Layer 3 devices. This enables a VXLAN to provide Layer 2 functionality while existing at Layer 3, the Internet Protocol (IP) address layer. VXLANs deliver greater flexibility than VLANs and can scale up to 16 million VXLAN segments per network.
These three examples of standardized network virtualization are all deployed on top of network infrastructure, such as routers, switches and cabling.
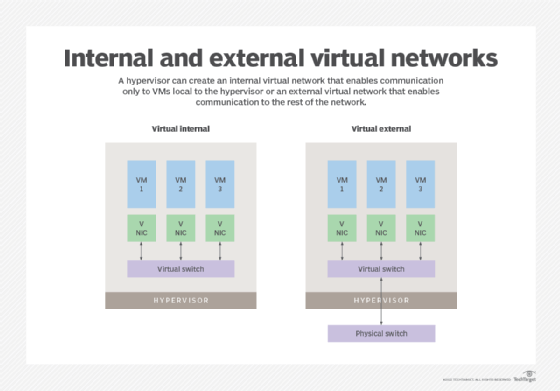
But another class of network virtualization is a bit more proprietary and happens deep inside a hypervisor that is running virtual machines (VMs). The hypervisor can create its own virtual network, either an internal virtual network that enables communication only to those VMs local to the hypervisor or an external virtual network that enables communication beyond the hypervisor to the rest of the network.
Benefits of virtual networks
Virtual networks provide key benefits to networking, including the following:
- Management. Virtual networks provide better access management by segmenting and joining devices virtually instead of managing these components only physically.
- Security. Better security is established by segmenting traffic and restricting access by groups, individuals or devices.
- Simplification. Virtual networking replaces hardcoded and rigid network routes with simplified, reduced paths that optimize access.
- IP mobility. VMs can be moved across the network easily to different hosts while maintaining their IP address, which aids disaster recovery and load balancing.
Challenges of virtual networks
Despite the benefits of virtual networks, they also have some potential challenges, including the following:
- Extra layers of management. The management of the network occurs at both the physical and virtual layers.
- Troubleshooting. Much like the management challenge, troubleshooting also happens at both the physical and virtual layers.
- Potential security exposure. The negative effects of misconfiguration can be amplified across a wider set of devices or users.
Examples of virtual networking
Some examples of virtual networking include the following:
- Load balancing. In order to maintain a more optimal traffic environment, many organizations rely on a load balancer. Virtualizing resources makes it much easier to address balance and move traffic.
- Hypervisor/virtual servers. Virtualization platforms, like VMware, Hyper-V and Xen, all virtualize networking resources within the hypervisor and externally for VMs that are connected to the rest of the network.
- Cloud computing. Connecting data centers to cloud-based applications generally demands some level of network virtualization, especially in environments where an application may live in multiple cloud zones for redundancy.
- Software-defined data center (SDDC). The SDDC strategy relies on network virtualization to create, at the data center level, a completely flexible pool of compute resources that can be dynamically deployed and reallocated based on need.














